

October 30, 2022
What are The Challenges of Cybersecurity In Healthcare?
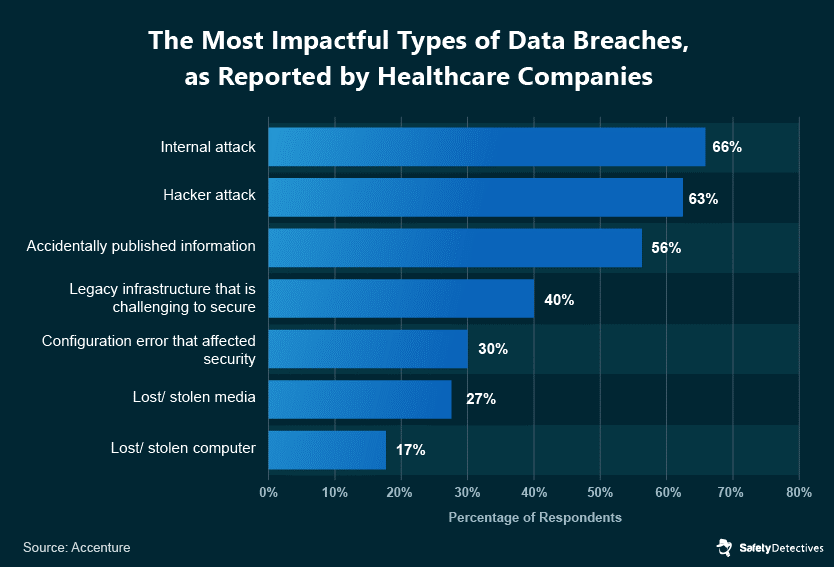
With reports of malware attacks that pose a threat to data safety via the Internet of Things (IoT) devices, medical cyber security executives must stay vigilant in their defense against threats. The recent report provides insight into changing healthcare data breach trends, forecasted threats for this year, and a roadmap on how to improve information technology (IT) resilience to prevent future healthcare data breaches. In recent times, the application of chatbot online has allowed for faster solutions to problems. Electronic health records kept in healthcare institutions are a prominent target for hackers due to the financial worth of patient health information. At each tier of a system. According to a report, Cybersecurity healthcare sector’s data creation growth rate would outpace that of any other economic sector until 2025.
The following are the top cybersecurity dangers that healthcare security officials should be aware of, according to the report:
- Medical equipment that is connected to the internet of things
- Telehealth and mobile health technology
- Remote patient access and the Cures Act
- Understaffed and underpaid IT departments
- Employee security training is lacking.
Modern hospitals are a colossal collection of healthcare-related data. To treat patients, all healthcare providers use linked medical equipment. Having safe access to biomedical devices is critical when they are used often. Unfortunately, most hospitals place little emphasis on this element, which leads to massive cyberattacks. According to a report, in 2020, there were over five million unprotected medical devices connected to the internet.
Steps That Must Be Taken to Curb Cyber Data Loss
Intact Policies
Every healthcare company should have written cybersecurity policies and governance procedures in place. Furthermore, every healthcare provider should save all paperwork relating to security policies, mandated actions, performed activities, and security testing evaluations for the previous years. Unfortunately, healthcare organizations do not devote enough effort to establishing protocols and developing thorough documentation. They believe it is a waste of time and reduces productivity. Contrary to popular belief, it is the cornerstone of a healthy tech environment.
Safety Of R&D
Research institutions and apps that produce private formulas for certain diseases are quite vulnerable. Healthcare organizations that are involved in R & D can face significant challenges and loss of money due to data breaches. a recent study found that the cost of bringing a new medicine to market is US $1 billion and it takes about 10 years for a product to reach the market. The stolen information such as patents and R& D data has a big impact on the company therefore such data is very confidential and must be protected. Telemedicine system development must incur tools that cater to such issues.
Issues Of Integrated Data
One of the difficulties in cyber security is the lack of a uniform data format. Healthcare organizations have amassed a variety of data formats throughout time, some of which are incompatible with technologies and other information.
Lack of data management: Another is that there is no comprehensive strategy for data management. Most of the time, the people who process a piece of data are not quite the same people who require and use the data. During the transfer, important details can be overlooked, and data ownership can be unclear.
Data privacy: data sharing misconceptions are also roadblocks to effective data integration. Some healthcare businesses have just a rudimentary awareness of data confidentiality rules. Data must be safeguarded from unauthorized access and alteration, but it must also be shared under certain conditions. It can be difficult to strike a balance between these two concerns.
Big Data To The Rescue
Big data can assist in the shift of healthcare from a reactive, care paradigm to a more integrated, preventative strategy. Data-driven decision-making can also help to accelerate the creation of customized ways for enhanced patient involvement, which might lead to improved compliance. Cybersecurity data can give information on health drivers for diverse groups of the population. The analysis of the data aids providers in developing evidence-based best practices. Gender, ethnic, and cultural prejudices, whether inherent or deliberate, can be eliminated via the proper use of health records.
Use Of CC
Cloud computing reduces expenses by enabling universal access to information across formats and regions. In addition to providing scalable storage options. Cloud storage also enables customizable security and data sharing using credentials. Cloud computing enables standardized, on-demand links to data in healthcare environments where up-to-the-second information can save lives, whether accessed from a doctor’s office, imaging center, hospital intensive care unit, or the scene of an accident.
Data mining: Data mining allows users to incorporate data from numerous databases and collecting systems so that it can be evaluated, analyzed, and used to plan and build more efficient care solutions if done correctly. With the use of modern technology, issues within the arena of technology can be resolved. Technicians belonging to all sectors must be vigilant to provide secure data analytics via data mining and Messenger Bot Ai techniques.







